We take security very seriously, and have deployed a host of features designed to prevent disruption.
DDoS mitigation
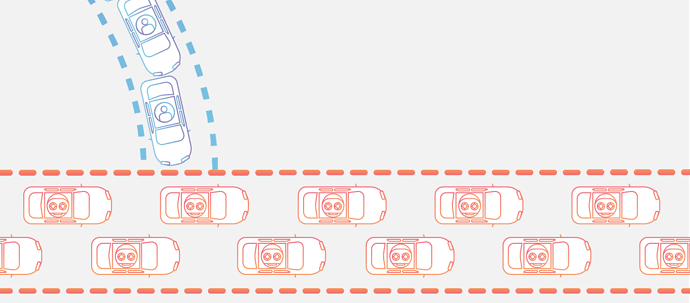
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.
Source
We employ cloudflare to mitigate any attempted DDoS attacks.
Two Factor Authentication
We offer users the option of securing their account via Two Factor Authentication (2FA).
This can be enabled it in your user preferences, and simply involves using a free Android or iOS authenticator app such as Google Authenticator on your smartphone to authorise any sign-in attempts, as demonstrated in the above video.
This stops anyone who may have your password from being able to sign in to your account.
Currently this option is optional for forum users, but we strongly recommend enabling it.
All Leaders, Admins and Moderators on this forum have to use 2FA.
100% open source platform
We have partnered with Discourse, who publish the source code for the forum software publicly. This primarily stimulates development, but also ensures that there are no nasty hidden things going on.
Security exploit bounty program
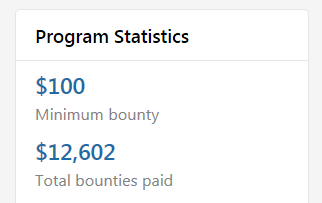
Going one step further than only publishing the source code, Discourse offer bounty payments for security holes found in the forum software.
This results in security experts continuously pouring over the source code looking for potential exploits.
If one is found, a bounty is paid by Discourse to the person who found it, and Discourse release a security patch.
Secure password storage
The PBKDF2 algorithm is used to encrypt salted passwords. This algorithm is blessed by NIST. Security experts tend to agree that PBKDF2 is a secure choice.
The hashing algorithm used is sha256 and number of iterations to run is 64000.
On-site and off-site daily backups
There are measures built into the forum to restore content and data should anything ever happen to corrupt it, but as a last resort we can fully restore the forum from backups that are made both on-site and off-site every day.
And much more…
Browser exploits, XSS and CSRF are all mitigated against as standard.